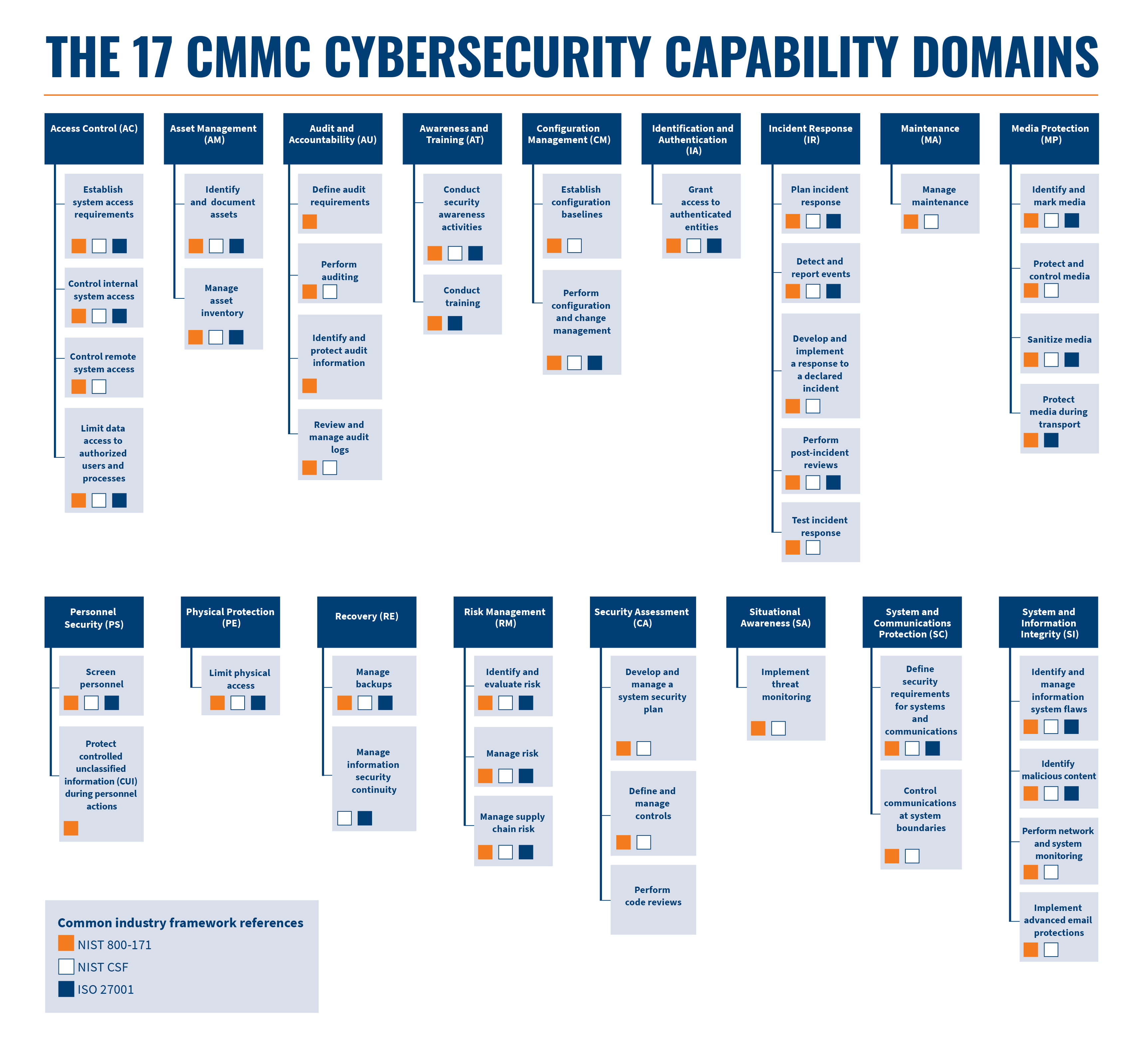
Cmmc Access Control Policy Example . Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. An 21 page document that includes the hierarchy of cmmc policies. It also includes the governed. Limit information system access to authorized users, processes acting on behalf of. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Navigating cmmc level 2 access control (ac) is essential for. We're left with something amazing in the end. Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. (they got rid of levels two and four.).
from flamlabelthema.netlify.app
It also includes the governed. Limit information system access to authorized users, processes acting on behalf of. An 21 page document that includes the hierarchy of cmmc policies. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). We're left with something amazing in the end. Navigating cmmc level 2 access control (ac) is essential for. (they got rid of levels two and four.). Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved.
Nist 800 171 Access Control Policy Template
Cmmc Access Control Policy Example (they got rid of levels two and four.). Limit information system access to authorized users, processes acting on behalf of. An 21 page document that includes the hierarchy of cmmc policies. Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). It also includes the governed. (they got rid of levels two and four.). We're left with something amazing in the end. Navigating cmmc level 2 access control (ac) is essential for. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved.
From devblogs.microsoft.com
CMMC with Microsoft Azure Access Control (1 of 10) Azure Government Cmmc Access Control Policy Example An 21 page document that includes the hierarchy of cmmc policies. We're left with something amazing in the end. Limit information system access to authorized users, processes acting on behalf of. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Configure conditional access policies to control the flow. Cmmc Access Control Policy Example.
From complianceforge.com
Defining CMMC & NIST SP 800171 Control Maturity Cmmc Access Control Policy Example Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Limit information system access to authorized users, processes acting on behalf of. An 21 page document that includes the hierarchy of cmmc policies. Navigating cmmc level 2 access control (ac) is essential for. It also includes the governed. Access. Cmmc Access Control Policy Example.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Cmmc Access Control Policy Example (they got rid of levels two and four.). It also includes the governed. Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Limit information system access to authorized users, processes acting on behalf of.. Cmmc Access Control Policy Example.
From www.dexform.com
It access policy template in Word and Pdf formats page 5 of 11 Cmmc Access Control Policy Example An 21 page document that includes the hierarchy of cmmc policies. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Limit information system access to authorized users, processes acting on behalf of.. Cmmc Access Control Policy Example.
From www.tenable.com
CMMC Authentication and Access Control SC Dashboard Tenable® Cmmc Access Control Policy Example We're left with something amazing in the end. An 21 page document that includes the hierarchy of cmmc policies. Navigating cmmc level 2 access control (ac) is essential for. (they got rid of levels two and four.). It also includes the governed. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Cmmc builds. Cmmc Access Control Policy Example.
From cksecuritysolutions.com
NIST 800171 CMMC Policy and Procedures Templates CKSS Cmmc Access Control Policy Example (they got rid of levels two and four.). Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. It also includes the governed. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and. Cmmc Access Control Policy Example.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Cmmc Access Control Policy Example Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. It also includes the governed. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. We're left with something amazing in the end. Navigating cmmc level 2 access control (ac) is essential for. (they got rid of levels two and. Cmmc Access Control Policy Example.
From www.totem.tech
CMMC Level 1 and FAR 52.20421 Basic safeguarding of FCI Cmmc Access Control Policy Example Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Limit information system access to authorized users, processes acting. Cmmc Access Control Policy Example.
From ntivaservicesit.wordpress.com
Access Control The Details on a Crucial Piece of CMMC Compliance Ntiva Cmmc Access Control Policy Example Limit information system access to authorized users, processes acting on behalf of. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. An 21 page document that includes the hierarchy of cmmc policies. Navigating cmmc level 2 access control (ac) is essential for. It also includes the governed. (they got rid of levels two. Cmmc Access Control Policy Example.
From locedos.weebly.com
Sample Information Security Policy Template locedos Cmmc Access Control Policy Example Limit information system access to authorized users, processes acting on behalf of. Navigating cmmc level 2 access control (ac) is essential for. We're left with something amazing in the end. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Access control (ac) guide [for cmmc level 2.0 compliance]. Cmmc Access Control Policy Example.
From flamlabelthema.netlify.app
Nist 800 171 Access Control Policy Template Cmmc Access Control Policy Example Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. (they got rid of levels two and four.). Navigating cmmc level 2 access control (ac) is essential for. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). We're left with something amazing in the. Cmmc Access Control Policy Example.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Cmmc Access Control Policy Example (they got rid of levels two and four.). An 21 page document that includes the hierarchy of cmmc policies. Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Limit information system access to authorized users, processes acting on behalf. Cmmc Access Control Policy Example.
From www.resmo.com
9 Access Control Best Practices Resmo Cmmc Access Control Policy Example Navigating cmmc level 2 access control (ac) is essential for. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Limit information system access to authorized users, processes acting on behalf of. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. (they. Cmmc Access Control Policy Example.
From devblogs.microsoft.com
CMMC with Microsoft Azure Access Control (1 of 10) Azure Government Cmmc Access Control Policy Example It also includes the governed. (they got rid of levels two and four.). Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Limit information system access to authorized users, processes acting on behalf of. Navigating cmmc level 2 access control (ac) is essential for. Cmmc builds upon dfars 7012 by verifying an organization’s. Cmmc Access Control Policy Example.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Cmmc Access Control Policy Example Navigating cmmc level 2 access control (ac) is essential for. (they got rid of levels two and four.). Limit information system access to authorized users, processes acting on behalf of. It also includes the governed. Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). Access control (ac) guide. Cmmc Access Control Policy Example.
From www.pinterest.com
CMMC Level 2 requires that an organization establish and document Cmmc Access Control Policy Example It also includes the governed. Limit information system access to authorized users, processes acting on behalf of. (they got rid of levels two and four.). Cmmc builds upon dfars 7012 by verifying an organization’s readiness to protect federal contract information (fci) and controlled unclassified information (cui). An 21 page document that includes the hierarchy of cmmc policies. We're left with. Cmmc Access Control Policy Example.
From cashier.mijndomein.nl
Access Control Policy Template Cmmc Access Control Policy Example Limit information system access to authorized users, processes acting on behalf of. Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. It also includes the governed. (they got rid of levels two and four.). Navigating cmmc level 2 access control (ac) is essential for. We're left with something amazing in the end. Cmmc. Cmmc Access Control Policy Example.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Cmmc Access Control Policy Example Configure conditional access policies to control the flow of cui from trusted locations, trusted devices, approved. Navigating cmmc level 2 access control (ac) is essential for. (they got rid of levels two and four.). Access control (ac) guide [for cmmc level 2.0 compliance] january 17, 2024 , cmmc. Limit information system access to authorized users, processes acting on behalf of.. Cmmc Access Control Policy Example.